The Department of Homeland Security strives every day to help federal agencies, state, local, territorial and tribal governments, and critical infrastructure asset owners and operators raise the baseline of cybersecurity. With the continuous growth of connected systems and rapid technology evolution, cyber vulnerabilities are being discovered in more devices and systems than ever before. DHS is committed to assisting manufacturers with security of their products through a steady stream of vulnerability information.
DHS sponsors a number of programs that are core components of vulnerability identification, response, and management practices around the world. They provide services and information to help users, system administrators, operators and manufacturers maintain safer, more secure software without government intervention. Each is publicly available and free for use by entities building or maturing their vulnerability management functions.
Listing Known Vulnerabilities
Sponsored by DHS Office of Cybersecurity and Communications (CS&C), the Common Vulnerabilities and Exposures (CVE) is the de facto global standard for the identification and definition of security vulnerabilities. The Homeland Security Systems Engineering and Development Institute (HSSEDI), which is operated by The MITRE Corporation, runs the CVE program that enables vendors to identify and communicate to their customers how vulnerabilities affect their products and services.
Each CVE is comprised of an identification number, a description, and at least one reference for the general public to know where the vulnerability has been publicly disclosed. The list of CVEs enables a diverse community of public and private stakeholders to effectively communicate and share vulnerability and exposure information.
Providing CVEs for unique vulnerabilities helps different product vendors track and fix vulnerabilities, and allows end users to correlate security update information for vulnerabilities discovered on their networks.
Multi-Party Coordination, Analysis, & Tools for Discovery
The CERT Coordination Center (CERT/CC), part of the Software Engineering Institute at Carnegie Mellon University, provides multi-party coordinated vulnerability disclosure services and produces vulnerability discovery tools. Multi-party vulnerability coordination and disclosure is the practice of coordinating a newly discovered vulnerability across a wide range of vendors and technologies at the same time.
The CERT/CC receives vulnerability reports from different kinds of researchers around the world and notifies the vendors who are potentially affected. CERT/CC also acts as a neutral third party to help develop mitigations (typically software updates) in an appropriate timeframe and publish actionable advice in the form of Vulnerability Notes.
The CERT/CC also develops and publishes open source tools to discover, analyze and diagnose software and system vulnerabilities. For example, CERT/CC’s Basic Fuzzing Framework and Tapioca tools have been used to find and help mitigate significant vulnerabilities in a wide range of applications, including thousands of smartphone apps.
Verified Data for Effective and Efficient System Maintenance
DHS and the National Institute of Standards and Technology co-sponsor the National Vulnerability Database (NVD) that performs analysis and provides expanded CVE entry information. This analysis provides data points such as severity scores, impact ratings, and enhanced search capabilities for users of the information. Also, it contains a record of each CVE-tagged defect and the associated fix or mitigation.
One of the important elements of the NVD is that it provides IT professionals with a rubric to measure the risk associated with known vulnerabilities and to prioritize system maintenance accordingly.
Coordination and Security Training for Control Systems and Medical Devices
The NCCIC Vulnerability Management and Coordination (VMC) team, through support from Idaho National Laboratory (INL), coordinates Industrial Control Systems (ICS) vulnerability disclosure. INL team members have unique expertise in assessing risks in critical systems and this collaboration provides the opportunity for DHS to act as a trusted third party in extremely sensitive disclosures.
In addition to assessing sensitive vulnerabilities in critical infrastructure, such as energy, food/agriculture or water systems, this collaborative team also reviews those that could result in hazards for critical manufacturing or in medical devices. Building a well-connected and capable community of practitioners, particularly in the private sector, has been instrumental in strengthening DHS’ coordination network for these types of sensitive vulnerabilities.
To help the ICS community improve their cyber defenses, the NCCIC offers training and procedures that teams can use in improving their ICS security and developing or their own capabilities. In FY17, NCCIC trained more than 1,400 professionals in ICS security either in on-line courses or instructor led classes at INL.
Continuous Improvement
DHS and its program partners are always evolving and adapting to keep up with the ever-changing and growing cyber vulnerability mission. Recent milestones and achievements include:
- The CVE Security Automation Working Group launched a pilot program in May 2017 to improve open, automated data sharing within the CVE Program and between HSSEDI and the CVE Numbering Authorities (CNAs). CNAs are organizations authorized to assign CVE IDs for products within a particular scope. Enabling CNAs to share detailed data more quickly benefits the entire program.
- The CERT/CC Vulnerability Analysis team established a one-day Vulnerability Response training course for project managers and others who may need to respond to vulnerabilities identified in their products. CERT/CC also published The CERT Guide to Coordinated Vulnerability Disclosure, a compilation of lessons learned based on their handling of vulnerabilities in the past three decades.
- At the NVD, NIST engineers have recently redesigned their data model, adding flexibility for new types of information and to improve search capability. The NVD is now finding ways to automate more data analysis and severity scoring through natural language processing and machine learning.
DHS recognizes community engagement as a critical component of discovering and correcting vulnerabilities before risks become incidents.
- To become a CNA, review the CNA Qualifications
- To request help coordinating a vulnerability that crosses multiple vendors or technologies, report it to CERT/CC.
- To be considered for receipt of vulnerability information in advance of public disclosure, complete the Vendor Statement Form (This is available to vendors only).
- To request help coordinating a control system or medical device vulnerability, report it to ICS-CERT.
To suggest additional topics for a series on cybersecurity and risk management, please contact: cscexternalaffairs@HQ.DHS.GOV

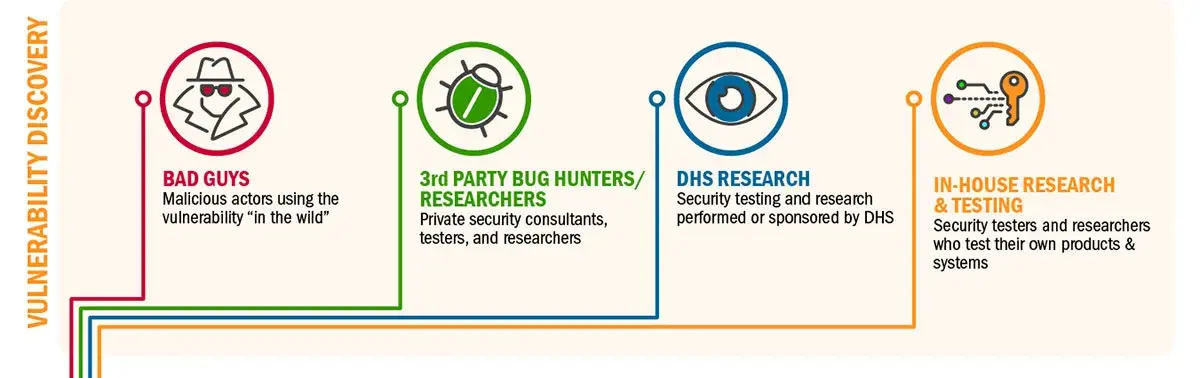
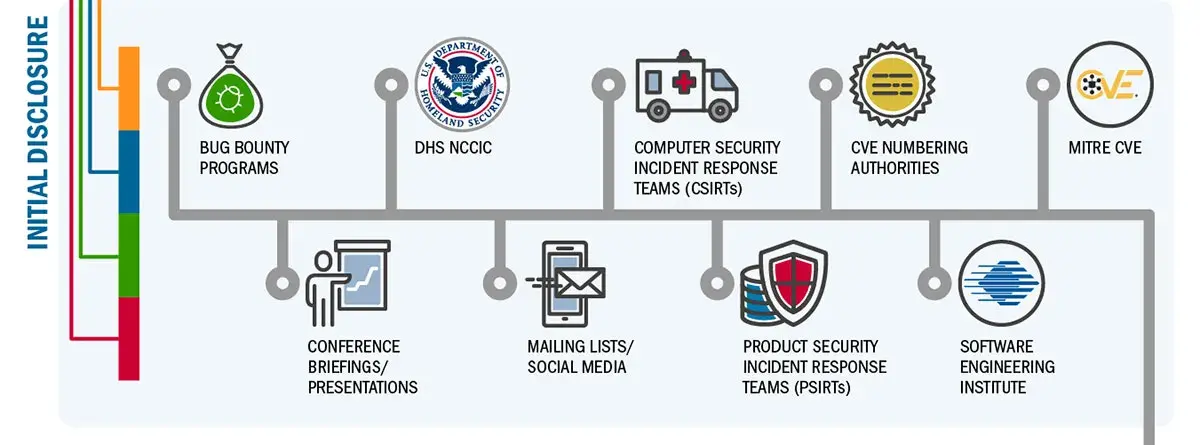
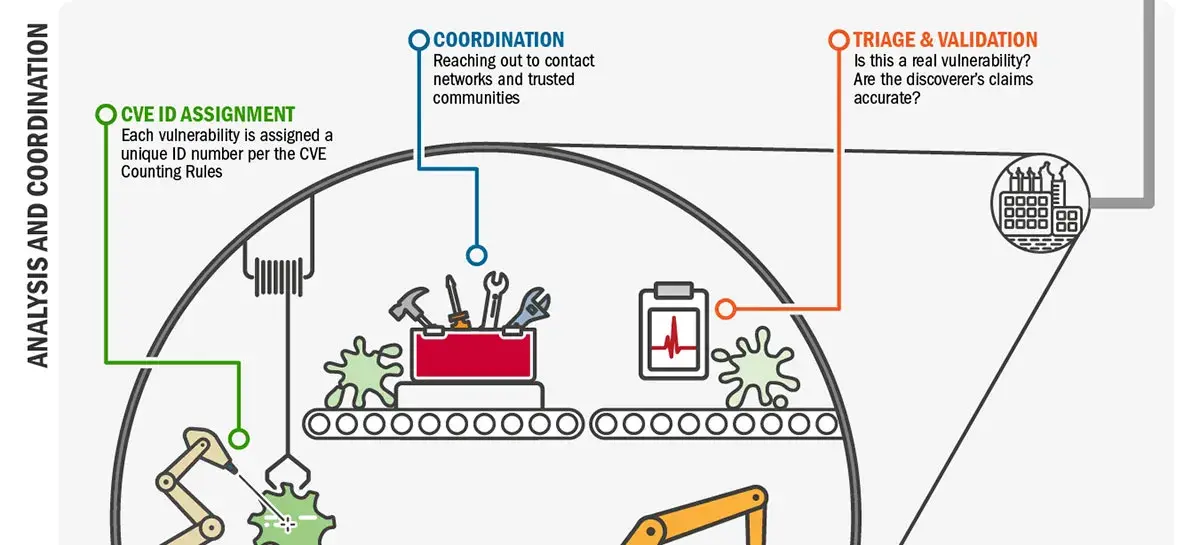
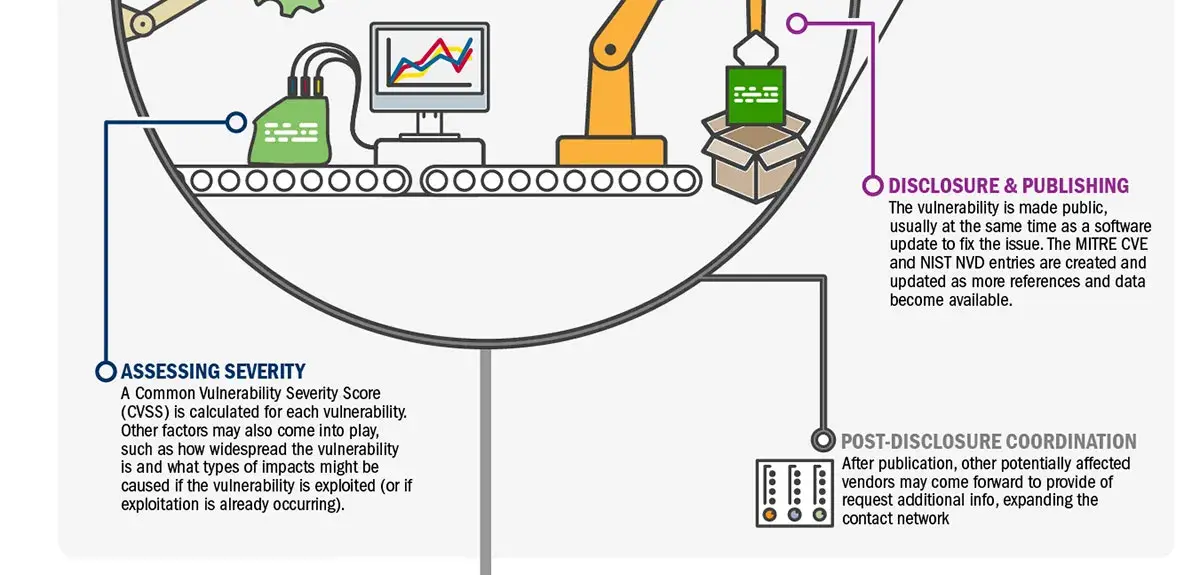

Download infographic (633KB JPG)

