Online child sexual exploitation and abuse (CSEA) is a serious crime that is never the victim’s fault. Stopping exploitation usually requires a victim to come forward to someone they trust — a parent, teacher, caregiver, law enforcement official or another trusted adult. This requires a lot of vulnerability from the victim. It is important to help them gather information to report the crime, choose an option with which they are comfortable and support them through this process.
To submit a report, you can do so through one of the following ways:
- Contact your local, state, or tribal law enforcement officials directly. Call 911 in an emergency.
- Call the Know2Protect Tipline at 833-591-KNOW (5669). All information received via the Tipline will be reviewed by appropriate personnel and referred to Homeland Security Investigations field offices for potential investigation.
- Submit a CyberTipline report with the National Center for Missing and Exploited Children.
When2Report
If you suspect that someone is exploiting or abusing a child, you should notify law enforcement authorities as soon as possible, whether the person you suspect is an adult, teen or child. For a deeper understanding of the threat, visit Know the Threats. You should file a report when someone:
- Harasses a child or teen or makes them feel unsafe online.
- Asks or pressures a child or teen to take pictures or videos of their private parts or to show their private parts on a video call or livestream.
- Threatens a child or teen by saying they'll share previous explicit images with others if the child doesn’t provide more photos or money.
- Creates, distributes or possesses child sexual abuse material.
NOTE: This is not an exhaustive list and experiences may differ. If you suspect a child or teen is being exploited or abused, report it — whether it happens once or multiple times, and whether you're certain or simply suspicious.
Reporting Tips2Know
Remember that online CSEA is never the victim’s fault and you should encourage children and teens to speak to a trusted adult. Check out these tips you can use to help children and teens if you suspect someone is exploiting or abusing them online:
- Victims of sextortion should never pay or send more images; doing so makes things worse.
- Save everything. Do not delete images, videos or texts — they will help the criminal investigators do their job. The more they know, the better they can help.
- The sooner you report the crime, the better. Reporting online CSEA can help stop the perpetrator before it happens to someone else.
- There is a way out for victims and support for survivors. Please visit the Survivor Support page for more information.
- Law enforcement officers are mandated to report suspected exploitation and abuse to child protective services. You can find your state’s child welfare organization here.
What Happens After a Report
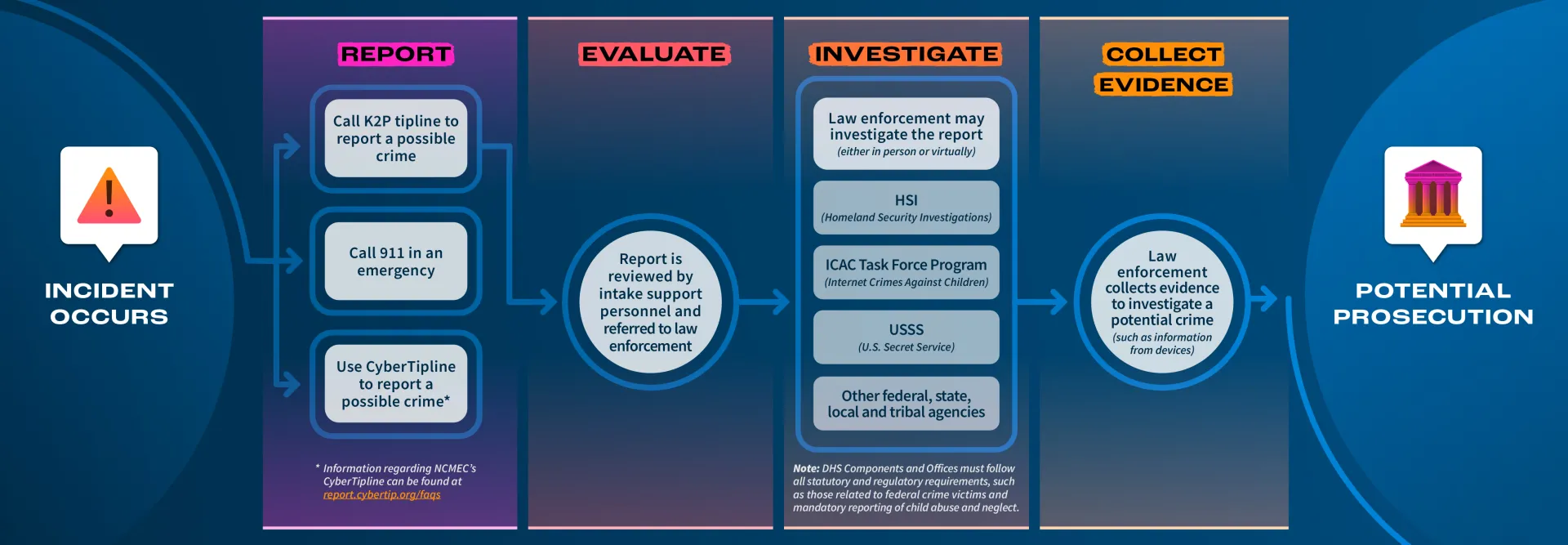
Remember: Reporting an incident helps law enforcement officials stop the harassment, arrest the offender and point the victim to support and other resources. Below is a detailed infographic of what happens when a tip is reported to the Know2Protect Tipline.
Depiction: All information reported to the Know2Protect Tipline is reviewed and referred to the appropriate government agency or local law enforcement for potential investigation. The agent or law enforcement official contacts the person who submitted the report to gather additional information about the case and collect evidence, such as electronic devices. Forensic analysts collect the information and evidence from the relevant devices using proper protocols and techniques to ensure the integrity and preservation of the evidence during the collection process and the protection of privacy for victims. If there is enough evidence, an arrest is made. This process is separate from any reports you make to tech companies, such as social media, messaging or gaming apps.
In addition to receiving reports from victims, sometimes law enforcement receives leads from tech companies that identify accounts distributing child sexual abuse material. These tech companies share pertinent information so that law enforcement can obtain search warrants and further investigate.
Download a high-resolution version of the infographic above.