In late March, the Cybersecurity and Infrastructure Security Agency (CISA) issued a warning that critical U.S. infrastructure sectors might be at risk of cyberattacks by Russian actors. Threats against our critical infrastructure aren’t new—physical threats and natural disasters have challenged our critical infrastructure and their support systems time and time again. However, the rapid development of new information and communication technologies, and their inevitable integration into our critical infrastructure, brings with it the possibility of digital attacks and other new challenges that we must be ready to face.
To help the country thwart potential cyberattacks, the Science and Technology Directorate (S&T) recently collaborated with the Center for Accelerating Operational Efficiency (CAOE), a DHS Center of Excellence (COE) led by Arizona state University, to convene subject matter experts (SMEs) and students from four other university-led DHS Centers of Excellence around the country to tackle real-life problem scenarios and identify practical solutions to current critical infrastructure risks and emerging threats. The COEs included the Critical Infrastructure Resilience Institute (CIRI) led by the University of Illinois; Criminal Investigations and Network Analysis Center (CINA) led by George Mason University; Maritime Security Center (MSC) led by the Stevens Institute of Technology; and National Counterterrorism Innovation, Technology, and Education Center (NCITE) led by the University of Nebraska, Omaha.
The third annual Grand Challenge Hackathon, held both in-person and virtually in late February, paired homeland security, critical infrastructure, criminal investigations, cybersecurity, and counterterrorism professionals with students in these fields, providing them with an immersive specialized learning environment and offering them opportunities to analyze and solve real-life homeland security problem sets. In doing so, the students were encouraged to consider pursuing professions in the homeland security science and engineering fields.
“As a COE, one of our primary missions is to provide cutting-edge educational opportunities to our students, and to encourage them to apply what they learn in the classroom to current events and issues that are impacting homeland security,” said CAOE Director Ross Maciejewski. “In order to do this, we’ve created and implemented a number of programs, one of which is our collaborative annual hackathon, which started in 2019.”
“These hackathons are unique, in that they offer participating students the opportunity to really develop their critical research, communications, and teambuilding skills, while also broadening their understanding of the Department of Homeland Security mission and how it operates,” said S&T Program Manager Eleanore Hajian.
This year’s hackathon focused on highlighting and solving three specific problem statements that addressed emerging threats to critical infrastructure:
- What are strategies for detecting if/when an autonomous vehicle has been hijacked or had its system compromised, and how can this hijacking be prevented or dealt with?
- How can we identify the presence of illegal activity on open-source networks, while simultaneously protecting our critical infrastructure?
- What actions (whether they be prevention, detection, or response) can be taken to mitigate attacks on digital elements of our nation’s critical infrastructure?
Participants were tasked with working collaboratively to plan, develop, and present viable solutions to each problem statement.
In total, 73 undergraduate and graduate-level students from across the five COEs and their affiliated universities participated in the hackathon. The students formed their own teams – each choosing one problem statement to address over the course of the weekend.
“The collaborative format of this hackathon created an engaging framework that enabled a diverse group of participants to not only work with each other, but to also learn from skill session leaders and mentors from across academia, industry, military, and DHS who were able to help them craft relevant and targeted solutions to their selected problem statements,” explained CINA Workforce Development and Education Lead Deanna Austin. “It also gave participants a unique opportunity to enhance their knowledge about real critical infrastructure issues that are challenging the security of our country.”
At the end of the event, each team presented their unique ideas to a panel of judges, all of whom were SMEs from the COEs, affiliated host universities, and DHS component agencies.
After judging, four of the teams were awarded a total of $10,000 in prize money for their innovative solutions:
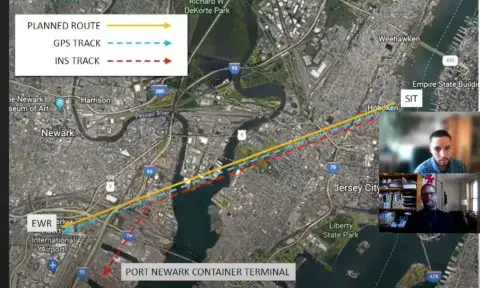
- Team MSC was awarded $3,000 for its winning solution to problem statement #1. Inertial Navigation Systems (INS) and Domain Awareness Communication Protocols to Facilitate Hijack Detection, proposed by two MSC students, would implement a security system to prevent potential bad actors from using “spoofed” (compromised) GPS signals to trick an autonomous vehicle into deviating from a pre-approved route. This system would enable an autonomous vehicle to share its GPS and INS signals (which tracks the vehicle and can’t be influenced by external factors) with relevant authorities. Any discrepancies detected between the two signals could serve as a warning that the vehicle has been compromised, and enable authorities to take appropriate action.
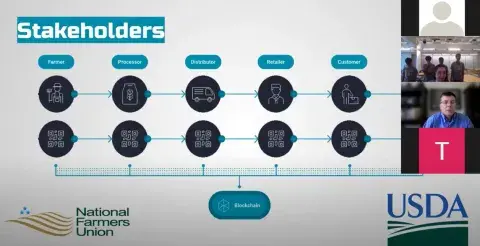
- Team Fulcrum (representing CAOE) was awarded $3,000 for its winning solution to problem statement #2. Blockchain and Asymmetric Encryption to Agricultural Supply Chains, proposed by five CAOE students, suggested utilizing blockchain technology (a decentralized, distributed ledger that records the origin of an asset) to enable distributors to keep shared records about where food has been shipped from and where it should be going, in order to prevent illegal activity (e.g., food fraud) as it travels through the U.S. supply chain.
- CINA ‘Team 7’ was awarded $3,000 for its winning solution to problem statement #3. The four CINA students suggested the use of low-budget, easily accessible cybersecurity protocols – specifically honey users (fake user accounts) and canary tokens (fake files that are designed to generate and send reports when they are accessed), that could be monitored for activities indicative of cyberattacks against critical pieces of infrastructure. In the event a cyberattack is detected, proper authorities could be notified and respond appropriately.

- Team L33TCOD3R5 (also representing MSC) received honorable mention and $1,000 for its solution to problem statement #3. With Asset-focused Security, the team’s six students recommended implementing routine risk assessment reports as a tool to prevent critical infrastructure cyberattacks. They suggested that data from these reports could be used to determine which pieces of critical infrastructure may be the most vulnerable to a cyberattack, so that targeted security measures could be focused and utilized accordingly.
With the success of this year’s hackathon, Maciejewski is already looking forward to the future. “Our hackathon had a tremendously positive impact on the education and workforce development missions of all the participating organizations, and the students who attended,” he said. “As we start planning for next year’s event, my primary goal is to get the rest of the COEs and their educational affiliates involved so that we can boost recruitment and participation among our minority serving institutions and students, and also broaden the variety of SMEs in the DHS space that attend as well.”
CAOE Education and Workforce Director Anthony Kuhn was impressed with the innovation that took place at the hackathon. “Each year, our participating students and SMEs continue to level-up in terms of the information that they share with each other, and the one-of-a-kind solutions that they propose to very real and current issues,” he said. “We look to continue this trend and ensure that our future events continue to be better and better.”
