Network Measurement Science is the efficient and principled application of scientific principles to network measurement. This project will develop innovative technologies to provide a system and capability to identify, classify, report, predict, provide attribution and potentially mitigate network/internet disruptive events (NIDEs). A NIDE causes a material loss or degradation of service, a material reduction in resilience or manipulation of traffic flows with adverse consequences. The Small Enterprise Assistance for Cyber (SEAC, pronounced “seek”) effort—part of the Predict, Assess Risk, Identify (and Mitigate) Disruptive Internet-scale Network Events (PARIDINE) research and development (R&D) project—will develop a cost-efficient delivery system for small businesses to improve the protection of their cyber footprint. The NIDE results will be combined with other tools and information—some of which have been developed by the previous DHS Science and Technology Directorate (S&T) Internet Measurement and Attack Modeling (IMAM) project—to provide access to cutting-edge tools and expertise in as near real time as possible.
Motivation
Internet attacks and disruptions often occur without much warning or many obvious pre-cursors. Attacks on availability ramp up over seconds or minutes. Unfortunately, the only viable defense organizations have – aside from generic protection mechanisms or heavy investment in fault-tolerant, distributed, high-availability infrastructure – is to rely on agile response teams and other intrusion-response capabilities to manually triage the event.
As currently practiced, attack detection swings into action after a disruptive event already has commenced. This approach cedes too much ground to an adversary, because it requires an organization to experience an attack before it begins to defend itself.
The goal of PARIDINE efforts is to develop innovative technologies that perform reliable predictive detection of emerging or unfolding NIDEs based on a thorough understanding of the characteristics of a variety of such events and the current internet state.
Approach
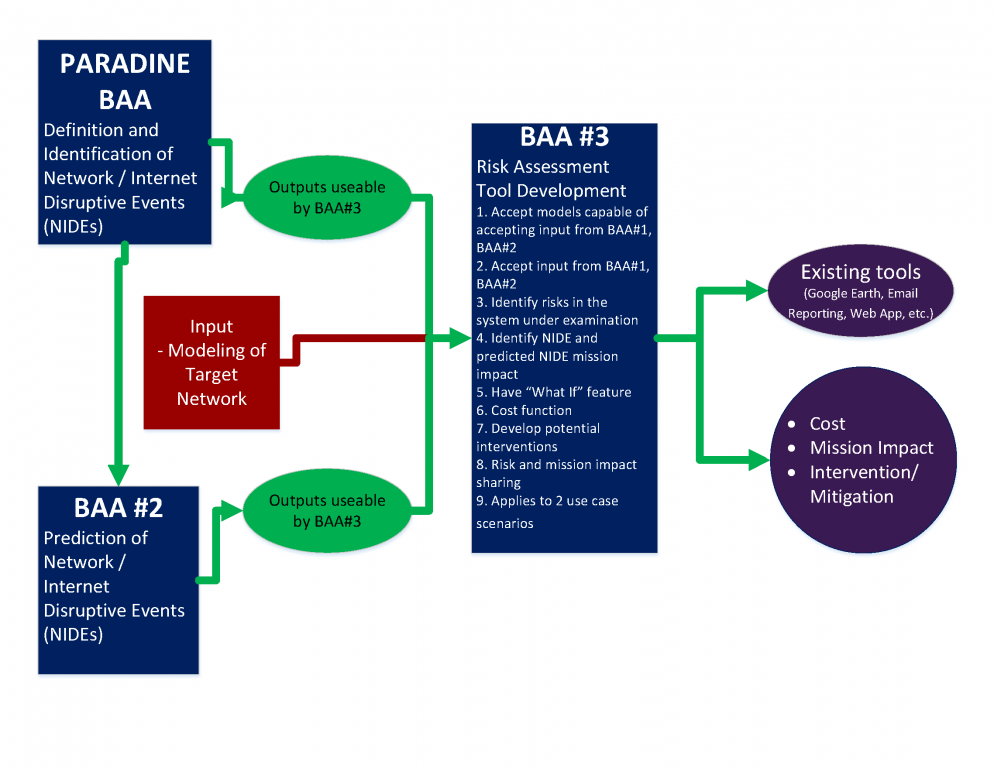
This project is designed to generate useful and actionable information that can define, identify, report on, predict and attribute NIDEs. NIDE reports are intended for network operators, large national or agency-level cyber-defenders, disaster planners, continuity-of-operations planners or small enterprises. PARIDINE efforts will also create a risk-assessment and mission impact tool specifically designed to use NIDE reports and system models to identify vulnerable points in networks or other systems and quantify the potential damage from plausible scenarios. As such, the potential customer base is anyone with a network that can be attacked and exploited. Customers will be able to use NIDE reports that includes attribution information to better defend their networks or understand events in retrospect. The risk assessment and mission impact tool to be created by the program requires a model of a system to apply the tool. This model may be highly mathematical and detailed or simple and more general, but it is always specific to the system under consideration.
SEAC customers are small-to-medium businesses where compromised cyber systems have high impact, but have limited resources to provide security. This customer set includes health care providers, state and local agencies that need to protect PII and other data and businesses in the critical infrastructure supply chain.
Performers
University of Southern California, Information Sciences Institute: Retro Future, Outages
The Retro-Future effort will record network state data called time travel, allowing replay of network security events called time travel—in essence providing an internet digital video recorder. The core capability improves recording and replay of network data to study network security events, while allowing that information to be shared across organizations within the privacy and policy constraints of each individual organization.
University of California, San Diego (UCSD): Science of Internet Security: Technology and Experimental Research (SISTER)
UCSD has designed, implemented, deployed and operated a secure measurement platform—Archipelago (Ark)—that supports large-scale active measurement studies of the global internet. SISTER demonstrates and illuminates the capabilities of the Ark infrastructure, resulting in documented explanations of structural and dynamic aspects of the internet infrastructure relevant to cybersecurity vulnerabilities, including macroscopic stability and resiliency analyses, transmission control protocol vulnerabilities, and physical-layer topology maps.
Brigham Young University: TrustBase [Link no longer valid, http://www.fht.byu.edu/research/trustbase]
TrustBase, is middleware on an open-source platform that supports improved web authentication including local and cloud-based authentication services, on mobile and desktop operating systems.
Oak Ridge National Laboratory: Visually Fusing Contextual Data for Situation Understanding (STUCCO)
STUCCO is a threat-intelligence platform that collects data from sources not typically integrated into security systems and extracts and organizes domain concepts into a knowledge graph to accelerate situational understanding of cybersecurity events. STUCCO leverages internal and external data sources to provide context to cybersecurity events in addition to a personalized threat view.
Pacific Northwest National Laboratory: Scalable Modeling of Network Flows (CLIQUE)
CLIQUE displays high-level overviews of network traffic using a new behavioral model-based anomaly detection technique. The CLIQUE system builds models for learning and classifying expected behavior of individual hosts on a network and compares these modeled behaviors to current data to generate early indicators of “non-normal” network activity.
Dissect Cyber, Inc.: Strengthening the Cyber Security of Critical Infrastructure through Discovery and Remediation of Vulnerable Supply Chain Organizations
Dissect Cyber scientifically researches and measures current practices within the critical infrastructure sector to identify cybersecurity gaps, test strategies and provide best practice recommendations. It also identifies high-priority critical infrastructures and their compromised or vulnerable supply chain affiliates, establishes a snapshot of the current state, and develops and tests robust mitigation strategies.
Oak Ridge National Laboratory: Situ/FASGuard, Combining Anomaly Detection with Signature Generation for Automated Cyber Defense
This pilot will integrate the Situ anomaly detection system with the FASGuard automated signature generation tools to provide active-response capability for zero-day attacks across organizations.
Charles River Analytics: Predictive Malware Defense
Charles River Analytics is developing a system for defending networks by predicting features of future malware, known as predictive malware defense (PMD). The new capability involves developing malware prediction software, signature generation software, and a streaming software prototype; evaluating the models and their general defenses; and creating a prototype predictive malware defense system.
Brigham Young University: Financial Sector Situational Awareness: Stock Markets
This effort develops strategies for securing the national equity market system by monitoring and detecting imminent risks, then developing optimal circuit breaker strategies across market centers.
Power Fingerprinting Cybersecurity: Automatic Detection and Patching of Vulnerabilities in Embedded Systems
Power Fingerprinting Cybersecurity enables security monitoring and integrity assessment on platforms that would otherwise not have the necessary memory or processing resources. This effort will demonstrate the feasibility of using PFP to perform automatic detection of exploited vulnerabilities and malicious intrusion in networked embedded systems.
GrammaTech: Multi-Abstractions System Reasoning Infrastructure toward Achieving Adaptive Computing Systems
This effort aims to create a mature and robust prototype for protecting and monitoring off-the-shelf software from cyberattacks by developing a tool for rewriting binary executables. The rewritten binaries will include monitoring and protection capabilities not included in the original binary code and remove vulnerabilities without changing the function of the software.
Red Balloon Security, Inc.: Symbiote Pilot
With DHS S&T funding (from both the Small Business Innovation Research office and CSD), Red Balloon Security has developed and successfully deployed the Symbiote technology. Symbiote, a firmware upgrade, can be embedded into existing systems, though the best place to install the product is in the supply chain manufacturing process. This first-of-its-kind technology provides protection that was previously unavailable.
BlueRISC, Inc.: Autonomous Detection and Healing of Silent Vulnerabilities
Silent vulnerabilities are vulnerabilities that are hard to detect in a network. Often these vulnerabilities do not leave evidence of compromise in a system. The Autonomous detection and healing of silent vulnerabilities effort is a new approach that will enable autonomous detection of exploitation attempts as well as healing of silent vulnerabilities. This next-generation tool identifies and displays software vulnerabilities with suggested code for remediation, enhancing the security of the software during development, when removal of vulnerabilities is most effective.
Centripetal Networks, Inc.: AI-Analyst: Cyber-Analysis Workflow Acceleration
This effort will research, develop and prototype intelligence automation technologies and applications that will accelerate cyber-analysis workflow processes. The ten-fold increase in analyst output addresses not only the alert-fatigue issue but also the lack of cyber analysts in the workforce, as fewer analysts are required when each analyst is more productive.
Resources
For the latest information about S&T Cybersecurity, visit the S&T Cybersecurity News, Publications, Videos and Events pages.
Video
2017 R&D Showcase: Mapping Our Way to a More Secure Internet
